3 Major Benefits of Implementing Automated User Provisioning For JD Edwards
Increased compliance regulations and the rising number of internal threats have forced organizations to tighten application access and adopt the principle of least privilege. However, when ERP applications like JD Edwards have thousands of users accessing them to perform their daily tasks, managing user access requests while adhering to compliance requirements can be challenging. The technical staff needs to put a considerable amount of time and effort into managing the provisioning process. And for auditors, providing audit reports showing appropriate approvals requires going through extensive paperwork. However, a majority of these problems can be solved through automated user provisioning. Here are three key areas where automation can significantly improve your JD Edwards provisioning process.
Streamlines User Provisioning With Configurable Workflows
Traditionally, granting access to JD Edwards users has been a manual process, with emails moving back and for between business owners and security/application admins. The large number of requests received by admins means there is little done in terms of manual checks. Essentially, the process is inefficient and allows risk to creep in due to overprovisioning. For auditors, this means going through volumes of paperwork to verify compliance and highlight risk.
However, automating your access provisioning process reduces much of the manual tasks, eliminates paperwork, and provides a streamlined process to grant access. An efficient provisioning solution allows you to tailor the workflow based on your company’s processes and hierarchy, with defined steps at each stage. Automation makes routine user and role administration and clean-up tasks faster. It also enables the setting up of a large number of users during implementation or acquisition projects.
Performs Segregation of Duties Checks Before Role Assignment
One of the biggest fallouts of manual user provisioning is over-provisioning, which leads to data security threats and increases the risk of fraud. Granting users new roles without checking for conflicts can provide users with more access than necessary. This could lead to segregation of duties violations and audit failures resulting in hefty fines.
This challenge can easily be overcome by deploying an automated user provisioning solution that also does SoD checks before granting roles. This allows approvers and admins to immediately identify SoD conflicts and program the process flow to allow or deny role assignments. Another significant benefit of automation is that the entire process is documented, providing a complete audit trail as evidence for your auditors.
Maintains a Detailed Audit Trail Of The Entire Process
Documenting and logging all access requests is a critical requirement for audit and compliance. However, tracking access changes through paperwork and tables is a tedious process. Not only does it increase the burden on your internal audit teams, but it also allows violations to go unnoticed. Apart from this, manual processes make it challenging for auditors to dig out information and provide evidence to external auditors.
Automation enables you to log all provisioning activity with a date and time stamp, allowing you to see exactly who requested, approved, and assigned what and when. This provides evidence for auditors who are testing that role assignments are authorized appropriately. It also provides evidence for internal inquiries or escalations if incorrect roles are assigned or if people perceive that undue delays have occurred.
Automated User Provisioning With Appsian
Appsian’s User Admin Manager (UAM) is an automated user provisioning solution that provides a configurable workflow that automates the process of requesting, approving, and provisioning roles, reducing the workload and paperwork involved. In addition, it can prevent unintended SoD violations by checking for conflicts before roles are assigned and keeps a full audit trail as evidence for auditors.
Download the Appsian User Admin Manager Data Sheet to learn how automation can simplify your JD Edwards EnterpriseOne user provisioning process and help you achieve better compliance.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
3 Key Steps To Prevent Fraud In Your JD Edwards EnterpriseOne
When you have a few hundred or maybe thousands of users logging into your JD Edwards EnterpriseOne applications – many of them handling critical financial data and transactions – fraud prevention measures are necessary. Here are three key steps you can implement to identify and prevent fraud in your JD Edwards EnterpriseOne applications.
Step 1: Identify The Gaps In Your JD Edwards Security
Securing your JD Edwards EnterpriseOne applications can be complex, especially since there are multiple routes by which users can access these applications. To prevent fraud and enhance security, you need to know what exactly users can access and the authorizations they possess.
So, the first step is to gain a complete view of all the users, the roles assigned to each user, the authorizations associated with individual roles, and how these authorizations are being used. Analyzing this information enables you to identify vulnerabilities created, overprovisioning, access risks, and compliance gaps.
Step 2: Implement And Maintain Segregation Of Duties (SoD)
Once you have a complete view of access and authorizations, the next step in preventing fraud is to have a detailed SoD policy in place. Segregation of Duties allows you to break down your workflow and implement checks at critical stages to prevent fraud. It decentralizes the power of approvals to ensure authorizations cannot be misused with malicious intent or for personal gain.
Once SoD has been implemented within your JD Edwards EnterpriseOne environment, running regular audit reports to identify users with access rights that violate your SoD policy is a crucial step. Since user roles keep changing over time, regular SoD audits enable you to maintain compliance. Where SoD conflicts are found, your internal audit team has to drill down to investigate and remediate the issues or, if appropriate, apply fully documented mitigating controls.
Step 3: Ensure That Your Reporting Is Current And Accurate
Reporting is an important part of any audit. Reports enable you to analyze data, gain insights, monitor progress, and provide evidence. However, using spreadsheets and manual checks is cumbersome and time-consuming. In addition, spreadsheets are notoriously prone to error, making them unreliable. Also, any changes made within spreadsheets can’t be audited.
An effective reporting tool enables you to slice and dice results for easier analysis, prioritization, and remediation. It also records changes in real-time and takes into account any SoD mitigations, thereby avoiding false positives. Lastly, detailed reports provide auditors with the evidence they need to prove compliance.
JD Edwards EnterpriseOne Fraud Prevention With Appsian
Segregation of Duties (SoD) controls are an important tool to prevent fraudulent activity or satisfy auditors’ demands. Unfortunately, JD Edwards EnterpriseOne contains no native functionality to help manage SoD or facilitate compliance reporting.
Appsian’s Audit Manager enables you to maintain an SoD model within the JD Edwards EnterpriseOne environment and runs regular checks to identify users with access permissions that might violate your SoD policy. It provides the ability to drill down to investigate any SoD conflict issue and remediate it with accurate information or, if appropriate, apply fully documented mitigating controls.
Download the Appsian Audit Manager datasheet to learn how you can control key fraud risks within your JD Edwards EnterpriseOne environment.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
4 Steps That Enable You to Prevent Fraud in Oracle EBS
ERP systems like Oracle EBS are at the core of financial operations for enterprises across the world. With hundreds of transactions occurring daily, it can be hard for audit and security teams to monitor all user activity. This necessitates a strong and strategic approach to identifying and preventing fraud. While there is no single solution that can help you prevent fraud, implementing the right combination of tools and solutions can enable you to identify vulnerabilities and mitigate fraud risk within your Oracle EBS environment.
How To Prevent Internal Fraud in Oracle EBS
Identify Vulnerabilities In Your Oracle EBS Systems
The complexity of Oracle EBS systems makes it difficult to track and monitor user activity. To protect access to critical data and transactions, security and compliance teams need to know who is accessing what. So, the logical first step in your fraud prevention strategy has to be a complete audit of your Oracle EBS applications to analyze your existing data security vulnerabilities. A detailed audit helps you identify weaknesses and provides insights into the improvements required to fill the gaps in your security.
Tip: Instead of burdening your existing security team, employ a third-party audit service that specializes in vulnerability and risk audits. This is a one-time exercise that can help you assess high-risk applications and locate blind spots that your teams may have missed.
Implement Segregation Of Duties
Segregation of Duties (SoD) is a well-established method to effectively reduce the risk of internal fraud. However, many Oracle E-Business Suite customers struggle to implement SoD with SQL reporting and complicated spreadsheets. Identifying role conflicts against hundreds of user roles in a dynamic environment can be time-consuming and an administrative challenge. Instead, opting for an automated SoD solution can help you instantly identify all existing role conflicts/violations and continuously monitor new validations as they occur.
Tip: Check for solutions that provide multiple options to resolve SoD conflicts by pointing out the best combinations of authorization roles.
Streamline User Provisioning
Provisioning plays a key role in ensuring your Oracle EBS users have access only to the data and transactions they require. However, granting user access requests while acquiring and documenting the appropriate approvals is a disjointed process. Also, without the right tools to check for potential Segregation of Duties conflicts before access is granted, new conflicts will inadvertently creep into the system. Streamlining your user provisioning process with an automated system enables you to set up an approval and review process that is documented. Not only does this reduce overprovisioning, but it also simplifies your audits.
Tip: Look for provisioning automation tools that also offer preventive Segregation of Duties checks.
Track And Audit Changes To Critical Data In Real-Time
The ability to monitor changes to data is crucial to identifying and tracking fraudulent activities. Visibility into master data changes, like bank accounts and supplier details, can provide auditors with the information they need to investigate and document potential fraud. While Oracle EBS allows you to audit all changes to selected tables, it does have an option to choose exactly which data and transactions should be audited. So, auditors may end up sifting through large volumes of irrelevant data. However, implementing a solution to track changes to data in real-time ensures that critical data changes are fully transparent. Since all changes to data are logged, you can take charge of your data and decide what to audit and monitor without having to go through hundreds of columns.
Tip: Choose a solution that not only monitors data changes by users but also provides before and after values.
Fraud Prevention in Oracle EBS with Appsian
Appsian enables you to analyze your existing Oracle EBS security without placing any demand on your technical team. It pinpoints weaknesses and makes recommendations to minimize fraud risks. Appsian’s Oracle EBS fraud prevention solution monitors user activity in real-time and logs all changes to the master data, enabling you to promptly investigate for signs of any fraudulent intention. The solution also triggers alerts and notifications to ensure such activities do not go undetected for long and result in huge losses.
Take a first-hand look at Appsian’s Oracle EBS fraud prevention capabilities. Schedule a demo with our ERP experts.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Oracle EBS Segregation of Duties: Why Automation is the Answer
When it comes to preventing fraud, segregation of duties is a key component of any compliance and risk strategy. However, enforcing SoD policies within your Oracle EBS applications can be riddled with several challenges, especially if you’re a large organization with thousands of users. From overprovisioning of users due to ill-defined roles to lack of visibility into user activity to tedious audit reporting, the entire SoD exercise can be a compliance nightmare. Ultimately leading to undetected violations, failed audits, and potential fraud.
Here’s how intelligent automation can help you streamline your SoD efforts, prevent fraud, and provide data to validate your compliance measures.
Detecting SoD Conflicts Before They Happen
Oracle EBS admin teams deal with requests every day to grant new roles and authorizations to users either because they are new or assigned new responsibilities. Every time this happens, manually verifying if the new roles result in SoD conflicts is practically impossible. The result? Overprovisioning and SoD conflicts that remain undetected and lead to an increase in fraud risk and audit failures. However, a simulation tool that provides a testing platform for potential violations can detect these conflicts immediately and send alerts to the admin/security teams. When integrated into your Oracle EBS systems, the simulation tool can also enable you to enforce SoD directly into your live environment.
[Tip: Look for a solution that not only alerts you to SoD conflicts but also offers possible solutions to remediate the conflicts so that business operations are not impacted.]
Automated SoD Analysis and Remediation
Automation helps you go beyond static rules that are built into preconfigured libraries. An advanced solution equipped with dynamic modeling and analysis can detect SoD risks based on risk patterns not just within your Oracle EBS environment but across multiple applications. With intelligent automation, you will be able to detect SoD conflicts, sensitive access, and potential policy violations for existing users immediately upon deployment.
Real-Time Auditing and Conflict Resolution
If you’re still using manual processes, conflicts and violations are usually detected after the fact. Automated SoD solutions can analyze user behavior and usage data paired together with vast amounts of historical data in the field of risk assessment to resolve conflicts as they happen. The continuous monitoring of user activity enables you to detect risky user behavior, even within the scope of user’s authorizations. This allows the auditing of specific violation events in real-time.
For example: A buyer who usually issues POs for $5000 suddenly starts to issue $10,000 POs. Even though the buyer in question has the authorization to perform the transaction, this could be a potential fraud risk. An automated solution enables you to flag this behavior for real-time for auditing and validation. Security and admin teams can also use the analysis to focus only on user activities. This allows them to remove redundant authorizations that are not in use, effectively de-provisioning users and mitigating risk.
Effortless Audit Reports
Auditing Oracle EBS roles and authorization can be tedious and time-consuming for internal and external auditors. Manually cross-referencing user activity against role conflicts to identify SoD violations is a huge auditing challenge. The process is inefficient, unscalable, and could lead to mistakes. Failure to detect SoD violations could have serious compliance ramifications for the company.
Automation helps eliminate a large part of manual data collection and analysis. Auditors can instantly access pre-defined risk reports, while security teams can receive automated reports on all roles containing an SoD violation. Users who have performed activities that violate SoD can be identified easily to initiate preventative and remediation measures.
Automate Oracle EBS Segregation of Duties with Appsian
The implementation of segregation of duties as a fraud prevention control is essential for any enterprise; however, detecting SoD conflicts, remediating them, and preventing violations is a whole other game. Appsian enables you to effectively implement SoD across your Oracle EBS applications with an automated solution that works in real-time to detect and prevent SoD violations. It continuously monitors all Oracle EBS user activity and authorization usage to deliver key insights and reports that enable your security and audit teams to implement SoD with significant savings in cost and time.
Schedule a demo with Appsian’s Oracle EBS specialists to understand how you can simplify your SoD journey with automation.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Appsian How-To: Easily Identify & Explore User-level SoD Violations in Oracle EBS
Automation is simplifying Segregation of Duties. In this video demonstration, you can see how Appsian can identify, explore, and resolve SoD violations in Oracle EBS and beyond. Leveraging user behavior profiling and actual usage data, Appsian turns the complex task of managing SoD into something you can handle with ease.
About Appsian
Appsian helps you comply with compliance regulations like Sarbanes-Oxley (SOX) by providing a single control point to manage and enforce segregation of duties (SoD) – across multiple ERP platforms.
Appsian is a full-suite solution that includes SoD rules definition, conflict analysis & resolution, real-time violation prevention, and detailed incident analysis. For example, if a violation is pre-approved, you can quickly create remediation (mitigation factor), so this violation will not appear again in the reports.
Appsian’s proprietary technology analyzes user behavior and usage data paired together with vast amounts of hands-on experience in the field of risk assessment to resolve conflicts. The solution can assess SoD risks and violations based on users’ actual usage, not only on their given authorizations. This allows the auditing of specific violation events in real-time. Of course, the best way to handle violations is to solve them clearly and quickly. Appsian features a conflict resolver tool that will remedy conflicting roles within a few seconds by pointing out the best combinations of authorization roles to change to solve the violations.
Appsian can also add real-time preventative SoD controls that stop violations at run-time – regardless of a user’s existing authorizations. This allows users with SoD exceptions to maintain the flexibility granted to them while ensuring no actual violations occur. In addition, these preventive SoD controls ensure that SoD rules are followed and drastically reduce or eliminate the manual reviews that were required using a detective approach.
Schedule your demo today and learn how Appsian can help your organization get clean and stay clean by eliminating the complexities in SoD.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Material Weakness Series Part 1: Ineffective Access Controls
This is the first article of a multi-part series featuring material weaknesses. Each piece will focus on one critical internal control weakness and provide solutions on how to resolve the weakness with granular security controls.
The purpose of an independent audit of a company’s financial reports, called a Financial Statement Audit, is to form an opinion by the independent auditor if the current and potential investors can rely upon the accuracy and completeness of the company’s financial statement. During this audit, the auditors will evaluate the design and operating effectiveness of the internal controls intended to manage the risks relevant to maintaining the accuracy and completeness of the financial reports. The auditor may identify deficiencies in the company’s internal control over financial reporting, which will be ranked from lowest to highest impact as Control Deficiency, Significant Deficiency, or Material Level Weakness.
What is a Material Weakness?
According to the PCAOB, a material weakness is “a deficiency, or a combination of deficiencies, in internal control over financial reporting, such that there is a reasonable possibility that a material misstatement of the company’s annual or interim financial statements will not be prevented or detected on a timely basis.” Companies with material weaknesses are required to report them in their public SEC filings in the period in which they were identified. There are multiple types of internal control weaknesses that could lead to a material weakness.
Access Control Weakness
Segregation of duty (SoD) security violations are among the most common examples of an access control issue in ERP applications that lead to an auditor reporting a material-level control weakness. The principle of SoD is based on appropriately segregating critical duties to more than one person. For example, a single person should not have the ability to create and approve vendors, nor should that same person have the ability to create and approve payments. These four access rights could easily lead to fraudulent activity.
Resolving SoD Security Violations with Appsian
The avoidance of SoD security violations within your ERP application starts with an effective user-provisioning process that enables organizations to proactively analyze the role assignments to verify that no SoD violation exists before authorizing the access assignment. Unfortunately, most organizations use manual user provision processes that are tedious and error-prone.
Appsian automates your user-provisioning, de-provisioning, and access recertification process and enables real-time detection and prevention of SoD violations. The Appsian Security Platform also continuously monitors user behavior and authorization usage. This allows organizations to de-provision unused authorizations and flag sudden deviations in user activity, thereby reducing the overall risk and enhancing threat detection.
-
Define Scope of Process
Choose what and whom to review. Activities, Authorizations, Roles, Employees and System
-
Commence Review
A list of authorizations is sent for approval then facilitated to the next level of approvers
-
Complete Review
Upon reaching a well-grounded decision, the next level of approvers are able to confirm with just one click
-
Seal the Process
Upon completing the process, the results are sent to the security managers to implement changes
Some of the other leading practices offered by Appsian to prevent SoD violations include:
Policy-Based Access Control
With policy-based access, organizations can go beyond roles to implement controls based on contextual attributes. A policy-based access control security model improves your policy enforcement capability at the SoD level.
Identity & Access Management (IAM)
Authorization, being an integral part of IAM, allows you to increase the effectiveness of your user-access management lifecycle process. By implementing dynamic MFA at the login, page, and data field level, you can ensure sensitive data and transaction changes are logged and protected.
Identity Governance & Administration (IGA)
With real-time user monitoring, you can remove unnecessary authorizations while gaining governance and oversight of all user access to increase your ability to detect and prevent SoD violations.
The Appsian Security Platform gives you complete visibility and control of your ERP applications from the inside to resolve critical material control weaknesses. See the Appsian Security Platform in action by scheduling a demo.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Preventing Risk from Privileged User Accounts: SAP, Oracle EBS & PeopleSoft
Organizations that use ERP applications like SAP, PeopleSoft, Oracle EBS, etc., manage thousands of users. Most of these users have limited roles that only allow them to perform their job-related tasks. But there exists a subset of users/accounts who are granted a wide spectrum of authorizations because their role entails managing the application itself: privileged users.
From an operations point of view, these roles are essential for the day-to-day functioning of the application to support the business. However, from a security perspective, the level of access and authorization granted to these privileged user accounts increases the overall risk exponentially. In fact, Forrester estimates that 80% of data breaches have a connection to compromised privileged credentials, such as passwords, tokens, keys, and certificates.
Who are Privileged Users?
Privileged users are users who are assigned roles and authorizations to perform functions that go beyond regular business transactions. These users include database administrators, network engineers, application developers, or third-party consultants. Their user accounts possess enhanced permissions that allow them to access sensitive data or modify key system functions. Also referred to as Superusers, some of the overarching privileges extended to them include:
- Full authorization to read, write and execute
- Creation or installation of files or software
- Modification of files and settings
- Deletion of users and data
Security Implications of Privileged User Accounts
Privileged users have a high level of access which means they will always be a target for attackers. If these accounts are compromised, it will lead to attackers gaining the same level of access.
Once inside, attackers can move from system to system undetected without leaving any digital footprint, making it harder to detect and stop. In addition, the attackers could gain access to an organization’s sensitive and confidential data, including company trade secrets.
If misused, either because of an error or with malicious intent, privileged user accounts can also inflict grave damage to a system or organization. Companies may have adequate security to prevent external threats, but privileged users are already inside the system. They can create backdoors, delete or modify data, override security settings, and more without detection.
According to the IBM 2020 Cost of Insider Threat Report, the average cost of an insider threat almost triples from $3M to $8.7M if the incident involves an imposter or thief who steals credentials and the costliest type of credential theft involves the theft of privileged users’ credentials.
Mitigating Privileged User Risk
Privileged users are granted greater access rights for a reason. They maintain and update applications that are critical for business operations. They are also responsible for a range of functions that require access to multiple servers, modules, and/or databases. This access also significantly increases the organization’s overall risk. However, this “privilege” can be counterbalanced with security measures that do not overly restrict them from performing their tasks.
Enforce Least Privilege Access
Many ERP applications provide role-based access controls and role-based authorizations. This means any user who logs in with valid credentials is granted all roles and authorizations assigned to that account. Thus, when a privileged user’s credentials are compromised, the attacker essentially becomes a privileged user giving them unchecked access.
However, by implementing attribute-based access controls (ABAC) through a dynamic policy engine, access can be allowed based on contextual attributes like location, time range, days, security clearance level, IP address, and more. For example, restricting privileged users to access only via your secure network ensures attackers cannot log in through an unknown network – significantly mitigating your risk while alerting you to failed access attempts.
Enforce Segregation of Duties (SoD)
Privileged user roles and authorizations should be regularly audited to ensure that they only have authorizations that are needed to perform their jobs. If the privileged user has not utilized a particular role within a specific timeframe, organizations should consider removing those privileges from the user. Since the user has never performed such functions before, they would not miss those privileges.
Even in cases where special privileges have been granted to perform specific tasks, a time limit should be set after which access is automatically revoked. These steps ensure that privileged users only have the necessary access at any given time and limit the organization’s overall risk.
Implement Step-Up MFA For Privileged Users
While your organization may have MFA at the login level, deploying step-up authentication for sensitive transactions at the page and data field level ensures that access to data and transactions is allowed only after the user has re-authenticated themselves.
Adding additional layers of authentication not only improves your security posture but also creates logs that can be monitored for suspicious activities. For example, a privileged user who is authorizing payment transactions can be easily identified during an audit since the user does not belong to the payroll or procurement team.
Behavior-based Profiling
Monitoring administrator accounts can help identify when one is compromised. However, large organizations may have hundreds of privileged users, and manual monitoring is virtually impossible. This is why Appsian Security’s unique algorithm combines multiple data sources to create a joint profile for each employee, including privileged users. The solution uses this business profile as the basis for optimization and as the behavior baseline.
This method is subsequently used to analyze irregular behavior, unused activities and authorizations, recommended authorizations for roles, and unoptimized license types. Privileged users who deviate from their normal usage can be easily monitored. For example, an anomaly is created when an SAP administrator who never accessed the customer database before tries to access it. Even though the user has the authorization to access the database, a deviation in behavior can be an indication of compromised credentials, giving security teams an impetus to check user behavior.
The IBM 2020 Cost of Insider Threat Report states that 29 percent of all credential thefts involve the theft of privileged users’ credentials. This proves that privileged users are primary targets for attackers because of their access privileges. Appsian Security mitigates the risk of high privilege credentials and sessions being exploited by bad actors by enabling you to implement multiple security measures like attribute-based access controls, step-up authentication for sensitive transactions, segregation of duties, and behavior-based profiling.
Schedule a demo with our security experts to find out how privileged user risk can be mitigated across your ERP ecosystem.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How ProfileTailor GRC Helped Global Shipping Leader, ZIM, Streamline Segregation Of Duties And Authorizations in SAP
ZIM Integrated Shipping Services Ltd., commonly known as ZIM, is a publicly held Israeli global container liner shipping company. The company operates over 100 management systems spread across the company’s global offices. Each system has multiple users running numerous applications, all consisting of different authorization systems. This scattered approach eventually led to siloed teams operating with their own rulesets and segregation of duties (SoD) policies, which stood in the way of effective internal audits within stipulated timelines.
The decentralized teams at ZIM needed a comprehensive GRC solution to streamline SoD, standardize context-aware controls, and customize authorization management solutions for their different locations without impeding productivity. Specifically, they needed a system that would:
- Control authorizations in a multi-regional, multi-system environment
- Manage authorization related processes effectively on all systems worldwide
- Comply with SoD in a complex environment
- Monitor activity in production systems
So the company turned to Appsian Security’s ProfileTailor GRC solution to improve their global, multi-system authorization layout and improve GRC compliance.
ZIM’s Transformation From Siloed To Centralized
ZIM’s transformation from siloed to centralized did not happen overnight. It was a large-scale, global roll-out with multiple milestones that Appsian played an integral part in.
Centralizing Control & Visibility Over Global Authorizations: ZIM now has centralized control over global authorizations in their complex multi-system environment with Appsian’s ProfileTailor GRC Solution. Additionally, they have generated Employee Cards consisting of authorizations on all applications from a single point of view. This is providing visibility to relevant managers in every location.
Identifying SoD Violations: ZIM’s BMC Remedy IT Management System seamlessly integrated with Appsian’s solution in the next phase. As a result, ZIM can now stop potential SoD violations in their tracks at the early stage of requesting authorizations, helping their teams streamline Segregation of Duties and stay compliant in the long run.
Automating & Customizing Authorization Review Process: With their authorization request policies cleaned up, unified, and customized for each location, ZIM is now operating with an automated authorization review process without disrupting the workflow. They are also able to save overhead expenses and have become audit-ready.
The Last Mile – Standardizing Contextual Access Controls: Presently, ZIM is equipped to control the access of the IT teams into production systems. With Appsian’s ProfileTailor GRC, they can now continuously monitor users in the production environment and allocate temporary roles for specific tasks.
Their teams can standardize every process in terms of access, authorizations, and policies while allowing exceptions (e.g., specific data privacy regulations) based on locations.
Streamline, Standardize, Customize: Appsian’s Framework Could Benefit You Too
Through a series of successful implementations with the help of Appsian Security, ZIM is now –
- Streamlining Segregation of Duties
- Standardizing context-aware controls
- Customizing for each region without workflow disruption
If your organization is working with siloed teams engaged in manual audits and approval processes, Appsian’s ProfileTailor GRC Suite is your one-stop solution to gain better control over access risks, SoD, compliance, and audit. It can be used as a stand-alone solution for streamlining, managing, and enforcing SoD or as part of a suite of compliance products.
ProfileTailor GRC is compatible with all leading ERP applications, including SAP, Oracle E-Business Suite, Oracle PeopleSoft, Microsoft Dynamics, and more. Best yet, it can be implemented rapidly and will not require any changes to monitored systems.
Contact us for a customized demonstration today and find out how Appsian Security can help you.
Related Reading: Full ZIM Case Study
Image source: Wikimedia Commons
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
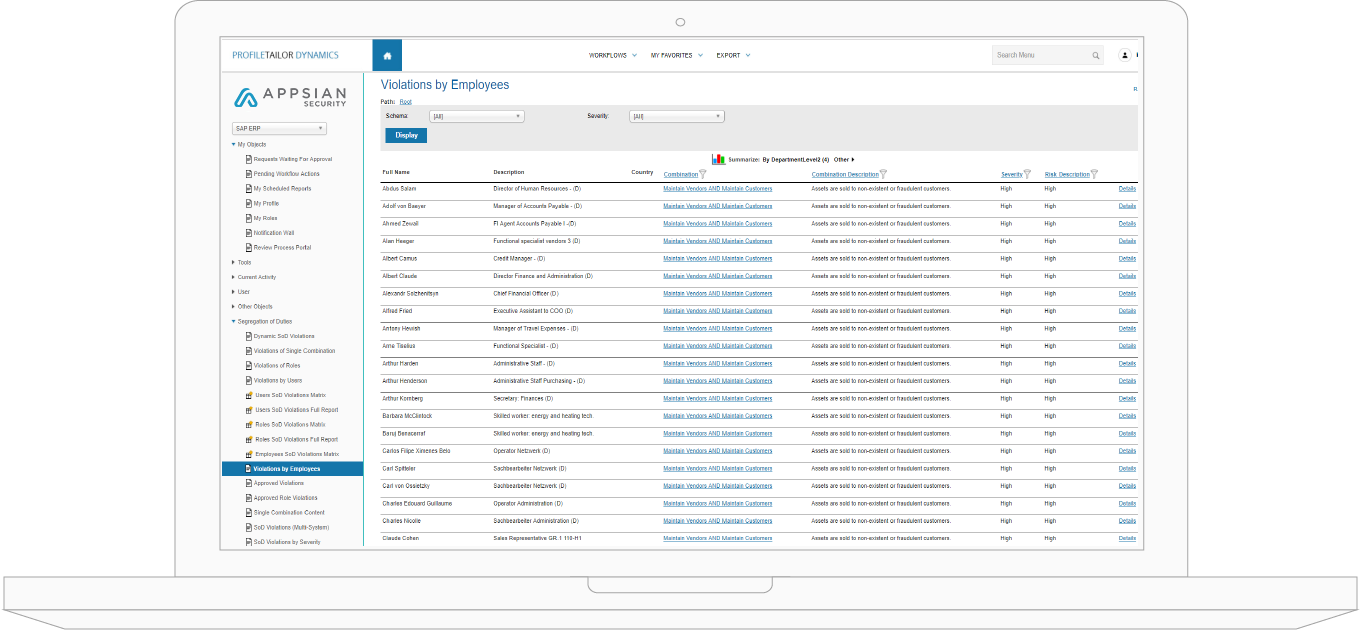
How Appsian Approaches Cross-Application SoD for SAP, Oracle & More
The concept of segregation of duties for SAP and other ERP applications is simple to understand: ensure that a user’s access privileges do not conflict or violate business policies and divide business processes between multiple users to limit the risk of fraud and error. However, the streamlining, managing, and enforcing of segregation of duties is far more complex. These days, organizations are turning to technology to help them automate tedious manual processes and reinforce internal controls—technology like Appsian.
Enforce Cross-Application SoD Rulesets from A Single Control Point
Appsian is a single control point that enforces cross-application SoD rules – allowing auditors and security managers to implement one SoD ruleset and enforce it on multiple applications simultaneously. They can also create rulesets for specific systems or change, activate, or deactivate SoD rules that can influence all systems together or only particular systems. Essentially, ProfileTailor GRC unifies all applications into one “language” so auditors and security managers do not have to try to understand each application’s jargon while giving them complete control over their SoD compliance, helping them comply with SOX regulations.
Maintain, Upload, and Download Rulesets in Multiple Schemas to Fit Different Scenarios
Ruleset maintenance is a focal point of any SoD implementation. ProfileTailor GRC includes various methods to create and maintain SoD rulesets easily and effectively to maximize the level of control over segregation of duties. For example, auditors can prepare a ruleset, upload it using a built-in mechanism, and then maintain the rules inside the application.
Alternatively, they can create rules in the application and then maintain, download, and upload them to Excel sheets. Further, auditors can lock specific rules for editing while allowing others to be opened. Business units can edit their own ruleset while being able only to view the organization’s global ruleset. Additionally, ProfileTailor GRC comes with a predefined ruleset that is ready for customization so organizations can be up and running almost immediately.
Resolve SoD Conflicts in Seconds
The best way to handle SoD violations is to solve them clearly and quickly. ProfileTailor GRC analyzes user behavior and usage data paired together with vast amounts of hands-on experience in the field of risk assessment to resolve SoD conflicts in just a few seconds. ProfileTailor GRC can audit violation events in real-time because it assesses SoD risks and violations based on users’ actual usage, not only on their given authorizations, and recommends the best solution for solving the violation and up to 5 additional possible solutions
Make ProfileTailor GRC a Critical Part of Your Compliance Strategies
ProfileTailor GRC can be used as a stand-alone solution for streamlining, managing, and enforcing SoD or as part of a suite of compliance products. This means that enforcing an SoD ruleset will influence other workflow processes. For example, provisioning/de-provisioning user accounts, requesting new authorizations and preventing SoD conflicts, opening new user accounts automatically without SoD violations, and business rules for granting or revoking authorization roles.
ProfileTailor GRC is compatible with all leading ERP applications, including SAP, Oracle E-Business Suite, Oracle PeopleSoft, Microsoft Dynamics, and more. It can be installed as an on-premise solution for continuous protection or in the cloud as a continuous inspection solution.
For more information on how ProfileTailor GRC approaches segregation of duties for SAP and Oracle ERPs or to receive a customized demonstration, please go HERE.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives