How Appsian Enhances SAP GRC with Cross-Application SoD & Risk Management
What is SAP GRC?
SAP Governance, Risk, and Compliance (SAP GRC) is a set of SAP solutions that enable organizations to meet data security and compliance standards. These solutions also provide control mechanisms to manage and mitigate risk. SAP GRC consists of four major components and multiple modules that manage risks, controls, identities, cyberthreats, and international trade across the SAP ecosystem.
What are the Components of SAP GRC?
SAP GRC features four major components that unify enterprise risk and control activities on a single technology platform. Each component has a set of modules that serve a specific function. As a whole, SAP GRC solutions give decision-makers the insights needed to adjust strategies and objectives while enabling them to predict, detect, and respond to business threats and opportunities. The four core components include:
Enterprise Risk and Compliance
Modules: SAP Risk Management, SAP Process Control, SAP Financial Compliance Management, SAP Business Integrity Screening
Cybersecurity, Data Protection, and Privacy
Modules: SAP Enterprise Threat Detection, SAP Privacy Governance, SAP Data Custodian
Identity and Access Governance
Modules: SAP Access Control, SAP Cloud Identity Access Governance, SAP Identity Management, SAP Single Sign-On
International Trade Management
Modules: SAP Watch List Screening, SAP Global Trade Services
Enhancing Your SAP GRC Capabilities with Appsian
While SAP GRC is a good tool to implement GRC across your SAP systems, it has certain noteworthy limitations. Appsian’s GRC solution goes beyond the SAP ecosystem to provide unprecedented visibility of real-time authorization usage and implement fine-grained, adaptive controls across applications. This significantly improves security while reducing fraud, risk, and exposure to sensitive data at an enterprise level. In addition, Appsian can be deployed as a stand-alone solution or combined with your existing SAP GRC solution to enhance security and risk management.
Here are some of the ways Appsian can enhance your GRC capabilities.
Cross Application Connectivity
Most companies utilize multiple ERP platforms for their business operations. Though SAP GRC offers a range of modules and controls, it can be deployed only within other SAP applications. Appsian integrates with several business applications like Salesforce, Workday, Oracle, Microsoft, Infor, or industry-related applications without any third-party connectors. Appsian GRC seamlessly connects all your applications to a centralized system for unified GRC management.
Attribute-Based Access Controls
Many ERP applications, including SAP, offer only role-based access controls. While role-based access works well when the user connects through a secure network like the office, today’s workplace demands a more adaptive approach to access controls. Appsian utilizes contextual attributes like location, device, time, IP address, and more to determine access risk and allows security teams to implement policies based on these attributes. Additionally, unlike role-based authorizations that are granted at access, Appsian’s fine-grained controls go beyond the point of access down to the data field and transaction level to deliver layered security, enhanced compliance, and improved user governance across multiple applications using a single control platform.
Authorization Management
As new users are added, and existing users are granted more roles, it becomes increasingly difficult to track and manage user authorizations, especially when dealing with multiple ERP applications. The result is user overprovisioning that creates greater data exposure, SoD conflicts, and overall risk. Appsian tracks authorization usage to recommend the elimination of unused and underused authorizations and access rights, making the monitored applications safer and simpler.
User Monitoring
While SAP GRC allows you to monitor and manage identities and control who has access to information, it provides little insight into what authorized users are doing within the applications. Appsian enables you to know what your users are doing, what tables they are accessing, what changes are being made, and by whom. It provides a detailed report of user activity data and allows you to set up alerts when sensitive information or tables are accessed.
Identification of Irregularities
The ability to continuously monitor user activity across applications also allows Appsian to track each user to identify and compare authorizations within each department or business unit for any discrepancies. The solution sends a notification to the management team of any suspicious activity that needs further investigation. However, the lack of user monitoring in SAP GRC means that such irregularities go unnoticed.
Impact on Licensing Costs
It is well-known that SAP licenses do not come cheap. Additionally, SAP does not provide a clear view of user roles and licenses. This makes it difficult to understand the cost impact of granting new roles/licenses to users. Appsian’s GRC solution considers licensing costs when recommending the best role to grant users by attaching costs to authorized roles and suggesting a less costly role when available. This allows you to manage your SAP license costs better and avoid overprovisioning.
Appsian’s enhanced approach overcomes the limitations of traditional SAP GRC, enabling you to manage identities, access, authorizations, and risk across multiple ERP platforms. Schedule a demo with our ERP GRC specialists to learn more about our GRC capabilities.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How To Handle Expiring SAP User Role Assignments
There are many reasons why SAP customers need to provide temporary access to their applications. These include short-term contractors or consultants, backup access when an employee is on vacation or suffering a long-term illness or disability, and emergency access scenarios. Regardless of the reason, organizations often encounter a common challenge: temporary SAP user role assignments expire without alerting the users. This lack of notification could potentially leave users locked out of applications or without the ability to perform their assigned tasks.
One of our clients, a leading multinational company based in Sweden, brought this to our attention and asked us to create an automated process for handling these expiring temporary SAP user roles.
The Challenges of Managing Expiring SAP User Roles with a Manual Process
Having to manually search through hundreds of thousands of profiles to find which roles have expired is time-consuming. In addition, it may lead to human errors and frustrated users. An automated role management solution effectively checks if a user still needs a particular role and automatically extends a required role or removes any unused roles.
For example, let’s consider an SAP user, Sarah. She has a role assignment expiring for her user ID in three days. She would not know that her ID expired until she logs in to the system on the third day and receives an error message. Next, Sarah must contact the helpdesk or her manager to request an extension. The approval process for this request could take 1-2 business days or more. The entire workflow would entail a series of manual processes and approvals. This would affect her ability to perform her daily tasks and negatively impact her productivity.
Use Automation to Prevent Temporary Roles from Expiring
Working with our client, Appsian Security created a process that automates how temporary SAP user role assignments are handled. It helps keep the users in control and accountable for their roles and authorizations while allowing them to extend roles if needed. In addition, the process ensures that users are not left without their roles, allowing them to continue performing their regular tasks. This helps improve the user experience and productivity for our SAP customers.
In a nutshell, Appsian’s automated role management and authorization solution helps SAP customers with the following:
- Fewer inquiries: Automating the SAP user role management and authorization process leads to fewer requests placed with the IT department and improves the turnaround time.
- Limited glitches: Users would no longer lose the ability to perform their usual duties due to the sudden expiry of temporary role assignments.
- Time management: Authorization managers no longer need to waste their time manually adding or removing roles.
- Automation: IT teams are relieved of manual approvals and processes.
- Resource management: Teams freed from time-consuming manual processes are better utilized for other functions.
- Documentation: All processes are now documented, making the workflow more efficient and audit-ready.
- Better user experience: With minimal glitches and less time spent on manual processes, there is a significant improvement in user experience.
Contact us today for a full demonstration of how to automate role management and authorizations in your SAP applications.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Appsian How-To: Enforce Transaction Level Policy Controls in SAP
The typical business application’s role-based access control (RBAC) security model provides poor dynamic transaction level policy control enforcement. In this video demonstration, you’ll see how to enforce transaction level controls in SAP using attribute-based access controls (ABAC). You’ll also see how Appsian Security’s analytics platform, Appsian360, allows you to monitor user behavior around those transactions and spot deviations from normal behavior.
Gartner recommends transitioning from the static RBAC security to Adaptive Security found in an Attribute-Based Access Control (ABAC) security model. ABAC allows you to set controls based on policies and enforce that control at the transactional level or at the field level. The good thing about this is we can enforce transaction level controls in one place, and we can make it work across the different transactions. In other words, it’s a one-to-many level of control.
You can then use Appsian360 to monitor the most often run transactions, where they are most frequently run from, and the active status of these transactions.
What is Adaptive Security?
Adaptive security is an approach to managing security that analyzes behaviors and events to protect against and adapt to threats before they happen. With an adaptive security architecture, an organization can continuously assess risk and control effectiveness monitoring and automatically provide proportional enforcement that can be dialed up or down to fit its need.
- Adaptive Security is configured using combinations of contextual attributes, to enforce policy requirements into the access controls, thus automating policy enforcement.
- Adaptive Security constantly monitors and analyzes detailed user behaviors at the transaction and data level to detect threats, and then adapts the security controls to respond to threat with a mitigation action.
- The specific policy requirements configured into the access controls become the “key risk indictors” that Appsian360 can monitor to detect and report anomalies and threats.
Contact us today for a full demonstration on how to implement policy controls at the transaction level in your ERP applications.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
SAP Access Management: Automating and Centralizing the Identity Lifecycle
If you do an internet search for the most common cause of data breaches, you’re going to get a variety of answers: ransomware, phishing attacks, stolen credentials, insider activity, etc. While these types of cyberattacks lead to data breaches, there is one simple truth ERP customers can never overlook: data breaches are caused by unauthorized access. Of course, not all unauthorized access is malicious. It can also be accidental due to poor access management (also called identity lifecycle management).
Clearly, the best practice is using the principle of least privilege to grant access to the applications, transactions, and data that a person needs to carry out their jobs. While data security and privacy are the primary elements of a successful access management process, the overall identity lifecycle management process should be automated, centralized, and provide IT teams and business units with audit-ready information. This information is critical for providing reasonable assurances that their SAP access management process is compliant and operating effectively.
Poor Access Management Exposes SAP Data to Risk
The process of SAP access management shouldn’t exist in a vacuum or a silo. Unfortunately, many organizations struggle with manual and decentralized identity lifecycle management. This leads to a variety of situations where unauthorized access leaves valuable ERP data exposed to risk:
- Unused new accounts with default passwords
- Employees collect new authorizations as they move around the business without removing unnecessary ones
- New employee authorizations causing SoD issues and sensitive access issues
- Employees leaving the company while their user IDs remain valid
- And many more
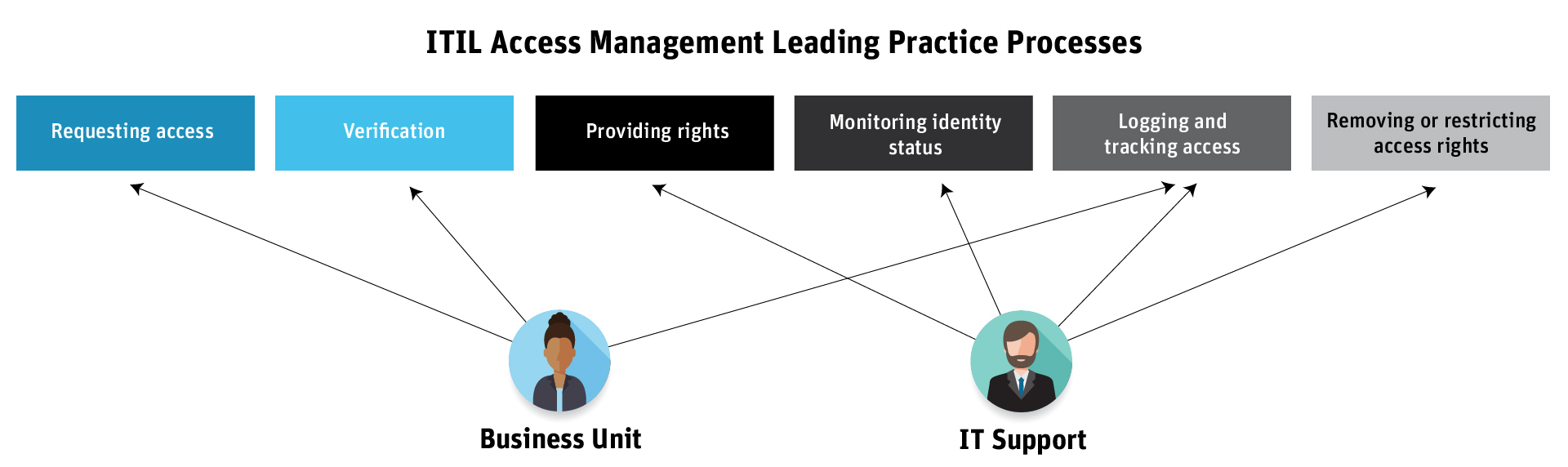
The identity lifecycle requires a process for controlling user access to critical information within an organization. The IT Infrastructure Library (ITIL) has a framework of best practices for access management: Requesting access, verification, providing rights, monitoring identity status, logging and tracking access, and removing or restricting access rights. But one department isn’t more responsible for the access management process than another, as outlined in this diagram:
While business leaders are the first line of defense and are responsible for owning and managing their risks, those business unit leaders and the IT departments are responsible for assigning and monitoring user privileges in ERP systems. Unfortunately, existing access management processes are manual, siloed, and error-prone. For instance, HR might request access by emailing IT or using a self-service portal to create a request. IT might use a provisioning solution that’s included out-of-the-box with their ERP system. But this approach is still mostly manual and exists in siloes, requiring one unit to rely on each other for updates.
This less-than-optimal approach leaves organizations exposed to security and compliance issues. Increasingly, organizations are under regulatory pressure to prove they are protecting access to corporate resources. As a result, organizations can no longer rely on manual and error-prone processes to assign and track user privileges.
Audit-Ready Access Management
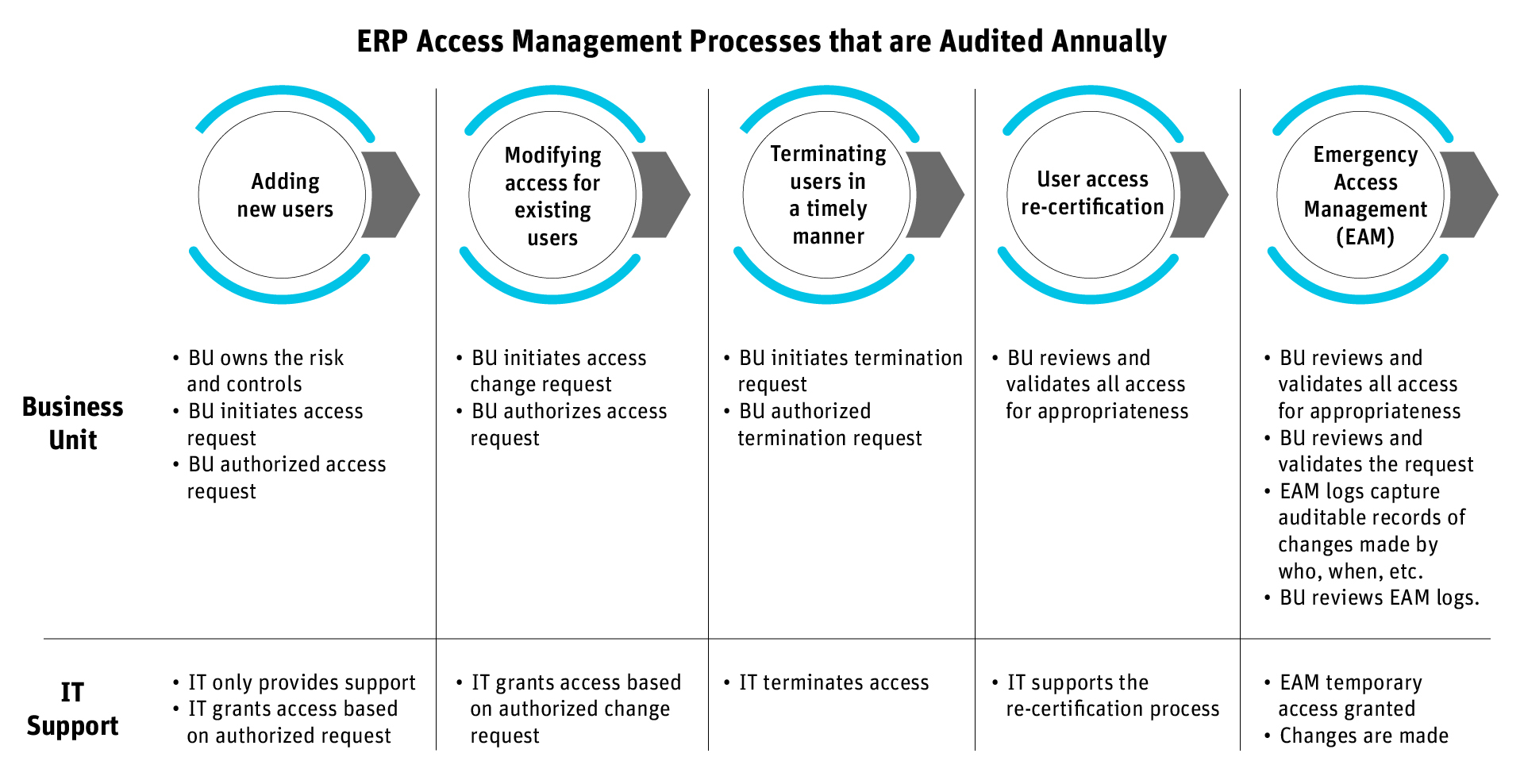
A poorly managed identity lifecycle process not only leads to security gaps but also visibility and compliance gaps.
As you can see from this illustration, all departments involved with access management will be audited to prove that their internal processes’ operating effectiveness sufficiently manages access risks, data security risks, and data privacy risks.
What’s missing for many organizations is an access management solution that centralizes and automates these tasks and enables granular access control and auditing of this process.
Automating and Centralizing Access Management with the Appsian Security Platform
Taking control of SAP access management from the start is key to enforcing data security, maintaining internal and external compliance, and adhering to various regulations. With ProfileTailor GRC from Appsian Security, you can easily organize, understand, and control the identity lifecycle process across your ERP landscape. Enabled by artificial intelligence, machine learning, and predictive analytics, it continuously identifies potential risks and provides optimized suggestions to streamline access management, including:
- Recommending the best alternatives when activities need to be removed from a user.
- Recommending the optimal segregation of roles to sub-roles according to business needs and actual usage. It automatically locks and removes the old authorization role from users who had it before the split.
- Solving SoD violations by replacing a user’s current roles without losing access to the activities actually needed.
- Choosing the optimal authorization role to grant users that enables them to perform additional activities without violating SoD policies.
Contact the SAP experts at Appsian Security for a demonstration on how you can prevent unauthorized user access at the transaction and master data level.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How ProfileTailor GRC Helped Global Shipping Leader, ZIM, Streamline Segregation Of Duties And Authorizations in SAP
ZIM Integrated Shipping Services Ltd., commonly known as ZIM, is a publicly held Israeli global container liner shipping company. The company operates over 100 management systems spread across the company’s global offices. Each system has multiple users running numerous applications, all consisting of different authorization systems. This scattered approach eventually led to siloed teams operating with their own rulesets and segregation of duties (SoD) policies, which stood in the way of effective internal audits within stipulated timelines.
The decentralized teams at ZIM needed a comprehensive GRC solution to streamline SoD, standardize context-aware controls, and customize authorization management solutions for their different locations without impeding productivity. Specifically, they needed a system that would:
- Control authorizations in a multi-regional, multi-system environment
- Manage authorization related processes effectively on all systems worldwide
- Comply with SoD in a complex environment
- Monitor activity in production systems
So the company turned to Appsian Security’s ProfileTailor GRC solution to improve their global, multi-system authorization layout and improve GRC compliance.
ZIM’s Transformation From Siloed To Centralized
ZIM’s transformation from siloed to centralized did not happen overnight. It was a large-scale, global roll-out with multiple milestones that Appsian played an integral part in.
Centralizing Control & Visibility Over Global Authorizations: ZIM now has centralized control over global authorizations in their complex multi-system environment with Appsian’s ProfileTailor GRC Solution. Additionally, they have generated Employee Cards consisting of authorizations on all applications from a single point of view. This is providing visibility to relevant managers in every location.
Identifying SoD Violations: ZIM’s BMC Remedy IT Management System seamlessly integrated with Appsian’s solution in the next phase. As a result, ZIM can now stop potential SoD violations in their tracks at the early stage of requesting authorizations, helping their teams streamline Segregation of Duties and stay compliant in the long run.
Automating & Customizing Authorization Review Process: With their authorization request policies cleaned up, unified, and customized for each location, ZIM is now operating with an automated authorization review process without disrupting the workflow. They are also able to save overhead expenses and have become audit-ready.
The Last Mile – Standardizing Contextual Access Controls: Presently, ZIM is equipped to control the access of the IT teams into production systems. With Appsian’s ProfileTailor GRC, they can now continuously monitor users in the production environment and allocate temporary roles for specific tasks.
Their teams can standardize every process in terms of access, authorizations, and policies while allowing exceptions (e.g., specific data privacy regulations) based on locations.
Streamline, Standardize, Customize: Appsian’s Framework Could Benefit You Too
Through a series of successful implementations with the help of Appsian Security, ZIM is now –
- Streamlining Segregation of Duties
- Standardizing context-aware controls
- Customizing for each region without workflow disruption
If your organization is working with siloed teams engaged in manual audits and approval processes, Appsian’s ProfileTailor GRC Suite is your one-stop solution to gain better control over access risks, SoD, compliance, and audit. It can be used as a stand-alone solution for streamlining, managing, and enforcing SoD or as part of a suite of compliance products.
ProfileTailor GRC is compatible with all leading ERP applications, including SAP, Oracle E-Business Suite, Oracle PeopleSoft, Microsoft Dynamics, and more. Best yet, it can be implemented rapidly and will not require any changes to monitored systems.
Contact us for a customized demonstration today and find out how Appsian Security can help you.
Related Reading: Full ZIM Case Study
Image source: Wikimedia Commons
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Solving Complex Security Challenges with Dynamic SAP Data Masking
It’s been a period of unprecedented change and adaptation for organizations of all sizes and in every industry over the past 18 months. During this time, I’ve had the opportunity to speak with many of our SAP customers about how they are managing their business risks and protecting their sensitive data. While the topics vary, I’ve noticed a recurring theme: there is a growing—and urgent—interest in using SAP dynamic data masking to strengthen data protection and enforce governance and compliance policies.
But what exactly do we mean by SAP “dynamic” data masking, and what are the best practices for using it to manage business risks and increase data security?
Dynamic Data Masking in SAP Starts with Attribute-Based Access Controls (ABAC)
Data masking is used to protect various types of sensitive and personal data stored in ERP applications, including intellectual property, personally identifiable information (PII), financial data, such as credit card, bank account information, and more. As traditional security perimeters dissolve and compliance requirements increase, protecting your ERP data is of growing importance. This is where dynamic data masking shines. Focused on protecting data at the UI-level in production systems, dynamic data masking can significantly reduce your risk exposure.
A Quick Clarifier: Often, data masking is used in non-production environments to protect ERP data copied from production. This technique is also known as data obfuscation, data scrambling, or data anonymization – and modifies the data itself – meaning it does not work for production systems. Dynamic data masking obfuscates information at the presentation layer (UI-level) without affecting the underlying data (at the database level).
Before dynamic data masking, traditional data masking policies used a static, role-based approach. For example, you include the role(s) and the field(s) in your rules – and a mask is always applied in all circumstances. While it minimized exposure, the static nature limited adoption as it would create barriers to data, and policies would have to be continually updated as users changed roles.
Dynamic data masking extends this policy logic by incorporating attribute-based access controls (ABAC), allowing flexible and wide-reaching rules to be created that incorporate identifiers such as role and other user, data, and access attributes. For example, user’s residency or security clearance, org code, IP address, location, and much more.
Static data masking versus dynamic data masking seems cut and dry. However, my conversations with SAP customers revealed two distinct approaches to using dynamic data masking: One focused on user attributes, and the other focused on the dynamic attributes of access and data itself. While the former allows simple, wide-reaching data masking that addresses functional risk, the latter enables a contextual, risk-based approach that truly balances data security with the needs of the business to access data.
Data Masking Approach #1: Wide-Reaching Policies Based on User Attributes
Many organizations start their data masking journey by analyzing how necessary it is for specific users to see specific data. Focused on functional risk, this approach aligns to least privilege and sets out to mask data that is unnecessary for a user’s job. For example, does a customer service rep need to see the full bank account info on an order? In most cases, no. Or should an HR manager be able to view the PII in a user’s profile from another business unit they are not responsible for? Certainly not.
Using dynamic data masking in these scenarios can deliver wide-reaching policies that incorporate user attributes such as role, business unit, org code, or country of residency. The ABAC technology allows data masking to be enforced “dynamically” when any activity that matches the defined conditions is present. (Meaning there is no need to make changes when users change roles, new users are created, etc.)
This approach is superior compared to the legacy approach that relies on static, role-based policies. Data exposure can quickly be minimized, and from a lifecycle management perspective, ownership is much simpler. However, data is still masked at all times for users, which means the practical scope of usage is still limited.
Data Masking Approach #2: Risk-Based Policies Based on Access Attributes
I’ve recently noticed a shift in thinking from policies based on user attributes towards those based on access attributes. Organizations might be realizing, thanks to the growing number of data privacy regulations and enforcement fines, that their data is now a liability, and they need to implement more risk-based masking policies based more on access attributes than user attributes.
Now an organization can leverage context-aware access controls to mask data in high-risk scenarios and show data in trusted scenarios. For example:
- Masking unpublished financial data from unknown IP addresses/locations
- Masking sensitive business data outside regular working hours
- Masking data for emergency access sessions
A recent use case for this approach to SAP dynamic data masking is on display at a Canadian rail company that needed to provide secure access to sensitive data to a hybrid workforce while also allowing access to self-service SAP modules on mobile devices for their remote workers traveling from city to city and connecting from wherever they have a Wi-Fi connection. They were able to enforce risk-based data masking policies based on access attributes such as location, IP address, time, data sensitivity, and more.
Protecting Data with SAP Dynamic Data Masking Solution
The more I speak with our SAP customers, the more I realize the different “definitions” they have about dynamic data masking. The more accurate definition is that SAP dynamic data masking uses risk-based policies based on access attributes. Without ABAC, companies must enable data masking with extensive customization, resulting in an unscalable ad-hoc solution.
Fortunately, the Appsian Security Platform’s (ASP) dynamic data masking leverages ABAC capabilities to provide fine-grained control over which sensitive data fields can be masked for any specified user in the context of any situation.
I invite you to contact the SAP experts at Appsian to learn how for yourself how we can improve SAP data security and reduce compliance risk with a fully dynamic data masking solution.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
SAP Access Controls: How RBAC & ABAC Work Together
To ensure employees remain productive in a dynamic and hybrid work environment, organizations use SAP access controls to allow their workers remote and secure access to ERP data, transactions, and self-service modules. Unfortunately, the existing SAP role-based access controls (RBAC) have reached their limitations in a dynamic workplace because static roles do not leverage contextual attributes.
Understanding SAP Access Control Using RBAC
Functionally, role-based access control (RBAC) is a policy-neutral approach to granting (or restricting) SAP access based on the roles of individual users in the company. Since RBAC was intended for on-premises data access from behind a corporate firewall, it creates a very strict, static set of permissions. You either have access or you don’t.
RBAC has always provided a strong foundation for setting SAP access controls. However, the way people are interacting with data resources is constantly evolving and RBAC is struggling to keep up.
Enhancing RBAC by Using Attribute-Based Controls in SAP
Organizations are looking for more flexible and secure ways to grant users access to only the information and resources they need to perform a particular task. This dynamic approach to SAP access controls enhances RBAC by considering different “attributes,” enabling security policies to be dynamic and “data-centric” and leveraging a user’s context of access to determine access to data. By incorporating these attribute-based access controls (ABAC), organizations can control user access more precisely, and better balance policy and security requirements.
The more attributes you can incorporate, the more precisely you can define what, how, and when a user or group of users can access data. Unlike RBAC, ABAC allows you to use contextual information such as project ID, company code, IP address, location, device type, and more to authorize access.
The RBAC + ABAC Hybrid SAP Access Control Model
Appsian Security extends and enhances existing SAP access controls by combining RBAC security capabilities with attribute-based policies. Starting with RBAC, organizations set the foundation of their access policies. ABAC begins the moment users start to access data and transactions and considers the context of access (who, what, where, when, and how) before allowing a user to access transactions or data.
The key benefits of the RBAC + ABAC hybrid model from Appsian Security include:
- Reducing Attack Surface
Organizations can reduce their amount of accepted risk by applying granular business policies and contextual access controls to strengthen data-level and transaction-level security. - Dynamic Data Masking
You can dynamically enforce data masking or outright restriction policies to any field in SAP when using real-time contextual policies that balance security and usability. - Reinforcing SoD Policy Violations
Adding ABAC to RBAC allows you to apply preventive controls in segregation of duties (SoD) exception scenarios. By doing so, you can prevent SoD violations while still allowing the flexibility of conflicting roles to be assigned (when necessary) and reinforces role-based policy to mitigate over-provisioning.
Without a solution like Appsian Security, the closest organizations can come to granting policy-based access to SAP is through customization or adding role derivations to a user for each attribute. Both options are costly and add complexity and overhead to role management in the long run.
Contact us today and schedule a demo to see how Appsian can help you enforce SAP access controls beyond the standard RBAC model.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
SAP Data Security Best Practices for ITAR Compliance
You know how vital SAP data security can be in the age of data privacy and compliance regulations such as GDPR, CCPA, SOX, and others. If you’re a company involved with any part of the defense supply chain—from direct contracts on defense projects to independent upstream suppliers of parts, components, services, and software that are ultimately used in defense products—you’re likely subject to ITAR compliance.
The International Traffic in Arms Regulations, or ITAR, is a set of government rules that control the export and import of defense-related articles, services, and technology on the U.S. Munitions List (USML) and ensure that sensitive materials (i.e., data) don’t fall into the hands of foreign parties and U.S. enemies. Put another way, if your company’s product, software, technical data, or services are identified on the USML, you’re going to be subject to ITAR requirements.
What Is ITAR Compliance?
Answering this question is a bit tricky because there is no formal certification process to become “ITAR Compliant” or “ITAR Certified.” Instead, companies are expected to understand the regulations and take the appropriate steps to comply with these requirements. We’re not in the business of offering legal advice, but the U.S. Department of State is an excellent place to start to learn more.
Ensuring that your SAP data security practices comply with ITAR mandates is essential from a security and consequence standpoint. You never want to compromise your data, but you also don’t want to face the risks of high fines and possible jail time for failing to comply with ITAR. The penalties for ITAR infractions are severe, including civil penalties up to $500,000 per violation and criminal fines of up to $1 million and/or ten years imprisonment per violation. (A California electronics company was recently fined $6.6 Million for multiple ITAR export violations)
What’s on the U.S. Munitions List?
There are 21 categories of Defense Articles in the USML as well as related technical data. For your reference, here are the categories (emphasis mine for #21):
- Firearms, Close Assault Weapons, and Combat Shotguns
- Guns and Armament
- Ammunition/Ordnance
- Launch Vehicles, Guided Missiles, Ballistic Missiles, Rockets, Torpedoes, Bombs, and Mines
- Explosives and Energetic Materials, Propellants, Incendiary Agents and Their Constituents
- Surface Vessels of War and Special Naval Equipment
- Ground Vehicles
- Aircraft and Related Articles
- Military Training Equipment and Training
- Personal Protective Equipment
- Military Electronics
- Fire Control, Laser, Imaging, and Guidance Equipment
- Materials and Miscellaneous Articles
- Toxicological Agents, Including Chemical Agents, Biological Agents, and Associated Equipment
- Spacecraft and Related Articles
- Nuclear Weapons Related Articles
- Classified Articles, Technical Data, and Defense Services Not Otherwise Enumerated
- Directed Energy Weapons
- Gas Turbine Engines and Associated Equipment
- Submersible Vessels and Related Articles
- Articles, Technical Data, and Defense Services Not Otherwise Enumerated
Regarding category 21, technical data refers to any data stored in your SAP ERP application containing information related to items or services designated on the USML. ITAR compliance centers on ensuring this data is not accessible by non-U.S. citizens, including employees, or inadvertently distributed to foreign persons or nations.
Add ITAR Compliance Items to Your Data Classification List
To comply with GDPR, SOX, and other compliance regulations, you probably have already classified which data in your organization is sensitive and subject to your data security, privacy, and governance policies. Further, with technical data, it’s also a good idea to tag each page with an ITAR notification. This prevents employees with legitimate access from accidentally sharing controlled information with unauthorized users.
Apply Policy-Based Access Controls
Now that you’ve identified and categorized your data, it’s time to establish who has access to it, when they can access it, from where, on what device, and how often. This is critical but challenging as any company with employees who are non-U.S. citizens or work with non-US subcontractors must prohibit them from accessing ITAR technical data. Adding to the challenge is SAP’s static role-based access controls (RBAC) for governing access because they do not leverage contextual attributes.
Appsian Security can help you create a more policy-based and robust data security program by enabling attribute-based access controls (often called policy-based access controls) that incorporate additional contexts, such as citizenship (nationality), certification, geolocation, network, time of day, and transaction type. Combining contextual attributes with your standard roles-based attributes, you can establish policy-based rules that grant access to ERP applications, technical data, and transactions only if the person meets certain contextual criteria while still allowing them full access to everything they need to do their job.
Leverage Policy-Based Controls to Configure Preventative Controls with Appsian Security
Once policy-based access controls are in place, Appsian Security can enable you to easily configure preventative controls at the SAP process, transaction, and field level to prevent unauthorized activity, enhance your data privacy, and increase the efficiency of your ITAR compliance program.
Avoid Unnecessary Data Exposure with Dynamic Data Masking:
An essential requirement of ITAR is ensuring that users accessing SAP applications, either in an authorized or unauthorized manner, do not have needless access to sensitive technical data through various pages, reports, or queries. Appsian can reduce the exposure of technical data with dynamic data masking while still allowing employees to do their assigned work.
Add Stepped-Up Multi-Factor Authentication at the Transaction Level:
Adding MFA at the transaction level ensures that users are not only authorized to access and view the data but perform the actual transaction based on their current context of access and not just their role. This should be applied to highly sensitive transactions like editing a direct deposit account number, accessing compensation data, or anything involving the USML.
Strengthen Data Loss Prevention:
Using context-aware data loss prevention policies, Appsian can prevent users from executing transactions that download technical data in high-risk scenarios, such as: citizenship, after business hours, from untrusted locations, networks, or devices. This prevents employees from downloading and accidentally sharing data they shouldn’t and prevents malicious insider threats from causing damage beyond non-compliance.
Enhance Visibility into ERP Data Access and Usage:
A critical component of ITAR compliance often lacking in SAP is real-time visibility into user behavior around data access and usage. Native SAP logging capabilities were not designed with data security in mind. Appsian360 allows organizations to continuously monitor data access and usage and proactively alerts security teams to anomalous activity, particularly useful for ensuring non-U.S. citizens are not accessing data they shouldn’t.
Learn How Appsian Helps You Enforce Controls in a Single Policy for Better ITAR Compliance
What makes ITAR unique from other data privacy regulations is the importance it places on citizenship, certifications, and network/location attributes. Appsian can help your organization capture these and other attributes and provide the tools for enforcing them in a single policy.
Contact the SAP data security experts at Appsian Security to find out how we can help you leverage policy-based controls to eliminate the complexities required with RBAC alone and more efficiently achieve ITAR compliance.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
3 Reasons Why You Need a Comprehensive SAP Role Audit Before a S/4HANA Migration
As SAP ECC customers prepare for their migration to S/4HANA, they are assessing the pros and cons of this transition in terms of cost, compliance, and data security. A critical step in an S/4HANA migration involves a thorough SAP audit of the existing roles and authorizations and optimizing license spends for the current users. Organizations need to consider three key factors during a complete SAP audit for better role management before an SAP S/4HANA migration.
SAP Role Audits Can Optimize Your License Spend
Many organizations still view their SAP licensing as a black box. They are ready to spend millions of dollars on SAP without understanding which licenses are being consumed or which licenses are required for each user. A common mistake many organizations make without realizing it is misclassifying users due to the lack of visibility into the usage of each employee.
A comprehensive role audit in SAP can help classify all users, accounts, and roles and eliminate those not in use, including the following best practices for optimizing license spend before the SAP S/4HANA migration:
Combine Users Between SAP Systems
Often, a single license is enough to access multiple SAP applications. Combining the same user across multiple applications frees up licenses that can be allocated to other users—preventing companies from paying double the amount.
Remove Inactive or Dormant Users
Certain users access the system only a few times a year, yet they are assigned Professional or Limited Professional License types. Since many corporations do not have visibility into the actual usage data for each role, account, or user, it is difficult to identify the inactive roles. By eliminating inactive and dormant users, organizations will be able to reallocate licenses to new users immediately, providing instant savings.
Classify All Users and Roles
Most SAP users utilize only a fraction of their allocated authorizations. Focusing on the actual usage of data based on the users’ roles ensures that companies will never be under or over licensed. In addition, by classifying all users, organizations can avoid the additional costs of Professional Licenses (used only by unclassified users).
SAP Role Audits Ensure Data Security Via Dynamic Access Controls
S/4HANA migration often opens up the “crown jewels” data to the security risks of the mobile world because the network firewall no longer protects it. You need to know what type of data is being exposed to your external users. That determines how you define the roles and how data is taken from the application and delivered to the users.
This requires applying protection to the user interface layer in terms of defining how you want the data to be viewed by different personas. Organizations conducting SAP audits need to enable dynamic access controls to gain visibility into:
- Where is a user coming from?
- What data are they trying to access?
- What device are they using?
- Is that device being used by the right person?
- What data are they trying to extract onto their device?
Periodic reviews and audits of the roles ensure that only the correct user having the proper roles can view the sensitive data that is otherwise encrypted or masked. For example, not every HR employee should have the role or access rights to view employees’ payroll data.
SAP Role Audits Are an Opportunity to Verify SoD Compliance
Organizations migrating to S/4HANA need to leverage SAP access controls or security monitoring solutions to perform periodic role and user analysis. The data collected during this audit can also help verify SoD compliance. Segregation of Duties conflicts, especially in financial and procurement transactions, are a significant reason for audit failures. Role audits could be used as an opportunity to collaborate with your organization’s compliance team to ensure that you’re securing your data and adhering to mandatory compliance requirements across your SAP ecosystem.
How Appsian’s ProfileTailor GRC Helps with SAP Role Audits
Migrating to S/4HANA remains a long and complicated process for organizations. The first big step is an exhaustive audit of the new and existing roles to facilitate effective role management in the SAP system. Role management offers access simulation capabilities, enabling administrators and role owners to perform a “what if” analysis at various stages of a role’s life cycle management and support compliant user provisioning. In addition, the system provides mechanisms for role design to reduce SoD conflicts and improve administration efficiency in SAP and other ERP and business applications. This usually includes a mechanism for transporting new or updated role definitions into appropriate application environments.
Appsian Security helps businesses with its ProfileTailor GRC Solution, ensuring cross-platform ERP data security, compliance, and SAP license optimization. It delivers unprecedented visibility of real-time authorization usage, helping companies optimize their spending before migrating to S/4HANA.
Want a secure and seamless transition to S/4HANA without spending a hefty sum on your licenses? Then, download our whitepaper, Critical Steps You Should Take Before Making the Move To S/4HANA, and reach out to schedule a demo with our SAP security experts.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives