How Appsian Enhances SAP GRC with Cross-Application SoD & Risk Management
What is SAP GRC?
SAP Governance, Risk, and Compliance (SAP GRC) is a set of SAP solutions that enable organizations to meet data security and compliance standards. These solutions also provide control mechanisms to manage and mitigate risk. SAP GRC consists of four major components and multiple modules that manage risks, controls, identities, cyberthreats, and international trade across the SAP ecosystem.
What are the Components of SAP GRC?
SAP GRC features four major components that unify enterprise risk and control activities on a single technology platform. Each component has a set of modules that serve a specific function. As a whole, SAP GRC solutions give decision-makers the insights needed to adjust strategies and objectives while enabling them to predict, detect, and respond to business threats and opportunities. The four core components include:
Enterprise Risk and Compliance
Modules: SAP Risk Management, SAP Process Control, SAP Financial Compliance Management, SAP Business Integrity Screening
Cybersecurity, Data Protection, and Privacy
Modules: SAP Enterprise Threat Detection, SAP Privacy Governance, SAP Data Custodian
Identity and Access Governance
Modules: SAP Access Control, SAP Cloud Identity Access Governance, SAP Identity Management, SAP Single Sign-On
International Trade Management
Modules: SAP Watch List Screening, SAP Global Trade Services
Enhancing Your SAP GRC Capabilities with Appsian
While SAP GRC is a good tool to implement GRC across your SAP systems, it has certain noteworthy limitations. Appsian’s GRC solution goes beyond the SAP ecosystem to provide unprecedented visibility of real-time authorization usage and implement fine-grained, adaptive controls across applications. This significantly improves security while reducing fraud, risk, and exposure to sensitive data at an enterprise level. In addition, Appsian can be deployed as a stand-alone solution or combined with your existing SAP GRC solution to enhance security and risk management.
Here are some of the ways Appsian can enhance your GRC capabilities.
Cross Application Connectivity
Most companies utilize multiple ERP platforms for their business operations. Though SAP GRC offers a range of modules and controls, it can be deployed only within other SAP applications. Appsian integrates with several business applications like Salesforce, Workday, Oracle, Microsoft, Infor, or industry-related applications without any third-party connectors. Appsian GRC seamlessly connects all your applications to a centralized system for unified GRC management.
Attribute-Based Access Controls
Many ERP applications, including SAP, offer only role-based access controls. While role-based access works well when the user connects through a secure network like the office, today’s workplace demands a more adaptive approach to access controls. Appsian utilizes contextual attributes like location, device, time, IP address, and more to determine access risk and allows security teams to implement policies based on these attributes. Additionally, unlike role-based authorizations that are granted at access, Appsian’s fine-grained controls go beyond the point of access down to the data field and transaction level to deliver layered security, enhanced compliance, and improved user governance across multiple applications using a single control platform.
Authorization Management
As new users are added, and existing users are granted more roles, it becomes increasingly difficult to track and manage user authorizations, especially when dealing with multiple ERP applications. The result is user overprovisioning that creates greater data exposure, SoD conflicts, and overall risk. Appsian tracks authorization usage to recommend the elimination of unused and underused authorizations and access rights, making the monitored applications safer and simpler.
User Monitoring
While SAP GRC allows you to monitor and manage identities and control who has access to information, it provides little insight into what authorized users are doing within the applications. Appsian enables you to know what your users are doing, what tables they are accessing, what changes are being made, and by whom. It provides a detailed report of user activity data and allows you to set up alerts when sensitive information or tables are accessed.
Identification of Irregularities
The ability to continuously monitor user activity across applications also allows Appsian to track each user to identify and compare authorizations within each department or business unit for any discrepancies. The solution sends a notification to the management team of any suspicious activity that needs further investigation. However, the lack of user monitoring in SAP GRC means that such irregularities go unnoticed.
Impact on Licensing Costs
It is well-known that SAP licenses do not come cheap. Additionally, SAP does not provide a clear view of user roles and licenses. This makes it difficult to understand the cost impact of granting new roles/licenses to users. Appsian’s GRC solution considers licensing costs when recommending the best role to grant users by attaching costs to authorized roles and suggesting a less costly role when available. This allows you to manage your SAP license costs better and avoid overprovisioning.
Appsian’s enhanced approach overcomes the limitations of traditional SAP GRC, enabling you to manage identities, access, authorizations, and risk across multiple ERP platforms. Schedule a demo with our ERP GRC specialists to learn more about our GRC capabilities.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Appsian How-To: Easily Identify & Explore User-level SoD Violations in Oracle EBS
Automation is simplifying Segregation of Duties. In this video demonstration, you can see how Appsian can identify, explore, and resolve SoD violations in Oracle EBS and beyond. Leveraging user behavior profiling and actual usage data, Appsian turns the complex task of managing SoD into something you can handle with ease.
About Appsian
Appsian helps you comply with compliance regulations like Sarbanes-Oxley (SOX) by providing a single control point to manage and enforce segregation of duties (SoD) – across multiple ERP platforms.
Appsian is a full-suite solution that includes SoD rules definition, conflict analysis & resolution, real-time violation prevention, and detailed incident analysis. For example, if a violation is pre-approved, you can quickly create remediation (mitigation factor), so this violation will not appear again in the reports.
Appsian’s proprietary technology analyzes user behavior and usage data paired together with vast amounts of hands-on experience in the field of risk assessment to resolve conflicts. The solution can assess SoD risks and violations based on users’ actual usage, not only on their given authorizations. This allows the auditing of specific violation events in real-time. Of course, the best way to handle violations is to solve them clearly and quickly. Appsian features a conflict resolver tool that will remedy conflicting roles within a few seconds by pointing out the best combinations of authorization roles to change to solve the violations.
Appsian can also add real-time preventative SoD controls that stop violations at run-time – regardless of a user’s existing authorizations. This allows users with SoD exceptions to maintain the flexibility granted to them while ensuring no actual violations occur. In addition, these preventive SoD controls ensure that SoD rules are followed and drastically reduce or eliminate the manual reviews that were required using a detective approach.
Schedule your demo today and learn how Appsian can help your organization get clean and stay clean by eliminating the complexities in SoD.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Material Weakness Series Part 3: Ineffective Transaction Level Controls
In the previous article of this series, we talked about data field-level controls and how you can resolve a data field-level control weakness with security best practices. This article goes one level deeper from ERP data fields to ERP transactions. Sensitive transactions like approving payments, adding vendors, and modifying contracts have a direct impact on the business. Without the necessary transaction level controls, they could create red flags during an audit, leading to discovering a material weakness.
What is a Transaction Level Control?
Transaction level controls are intended to detect and/or prevent errors, misappropriations, or policy non-compliance in a financial transaction process. Effective transaction-level controls help organizations achieve their mission and strategic objectives for a given business process transaction by appropriately mitigating inherent risks. Weak transaction controls could lead to fraud, mishandling of payments, or financial errors that eventually impact the company’s annual or interim financial statements.
How to Resolve Transaction Level Control Weaknesses
Resolving transaction level control weaknesses requires implementing specific solutions that enable you to create a security layer at the transaction level of your ERP application. A simple and direct method of achieving this is implementing Multi-factor Authentication (MFA) at the transaction level. While many organizations use MFA to secure ERP access, the authorization granted during login gives the user unlimited access to transactions related to the user’s role.
However, by deploying step-up MFA for sensitive transactions, you can re-authenticate identity and monitor and create an access log for these transactions. This also helps security teams flag suspicious transaction activity by the user, thereby adding a preventative and detective control at the transaction layer of your ERP application.
Implementing Transaction Control with Appsian
The Appsian Security Platform allows you to force MFA challenges at the transaction level to ensure Zero Trust, not just at the initial access but also deeper within your ERP applications. Appsian also enables you to go beyond Role-Based Access Control (RBAC) security models to a dynamic security model like Attribute-Based Assess Control (ABAC). The platform considers a user’s contextual attributes like access location, time of the request, device type, etc., before establishing trust and granting access to data or transactions. Your security teams can use these dynamic user privileges to enforce multi-factor authentication for partial or full access to sensitive data and transactions
The Appsian Security Platform natively integrates into your ERP web server without requiring customizations or additional servers. Security teams can use their existing MFA Vendors like Duo Security, Okta, SafeNet, Microsoft Authenticator, and more to force MFA challenges at the ERP transaction level.
Schedule a demo with Appsian ERP experts to understand how you can implement layered security controls inside your ERP applications to protect sensitive transactions.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Material Weakness Series Part 2: Ineffective Data Field Level Controls
In the first article of our material weakness series, we addressed what a material weakness is and how an ineffective access control weakness can be resolved. This article will look at another critical control weakness that can occur at the data field level.
What are Data Field Level Controls?
Field-level security settings, or field permissions, are intended to control whether a user can see, edit, and delete the value for a particular field on an object. These are the ERP data security capabilities that allow organizations to protect sensitive fields such as a candidate’s social security number without having to hide the candidate object. However, when these field-level controls are not configured correctly, users may be able to see sensitive personally identifiable information required by compliance regulations like CCPA and GDPR to be safeguarded.
How to Resolve Data Field Control Weaknesses
Protecting data at the field level is crucial from a data integrity and data privacy point of view. Here are six steps you can take to enhance field-level controls within your ERP applications:
- Implement the Zero-Trust security model that enforces the principle of never trust, always validate.
- Effectively using Multi-Factor Authentication (MFA) and enforcing MFA at various layers – login, critical transaction level, and critical data field level to enable layers of security.
- Implement layered security, also known as defense in depth (DiD), in overlapping layers of controls that typically provide the three control capabilities needed to secure assets: prevention, detection, and response. While no individual security control is guaranteed to stop 100% of the cyber threats, layered security provides mitigations against a wide variety of threats while incorporating redundancy or compensating controls in the event of a control failure.
- Transition from static security found in Role-Based Access Control (RBAC) security models to a dynamic security model like Attribute-Based Assess Control (ABAC) that enables the enforcement of policy requirements into the access controls at the transaction and data level.
- Design dynamic security controls capabilities to improve their ability to identify, detect, prevent, and respond to anomalies and threats.
- Perform periodic control assessments to validate the effectiveness of the existing controls.
Protecting Data Fields with Appsian Security
The Appsian Security Platform has been designed specifically to address security and governance challenges that companies face within their ERP ecosystem. Appsian offers a range of solutions that enable you to implement Zero Trust security. From multifactor authentication at the login level to masking of sensitive data fields with the ability to reveal data only after authentication, Appsian provides complete control over data access and data exposure that goes beyond the initial access.
Appsian’s attribute-based access control also ensures that authorizations are not absolute. It considers the context of access when allowing or restricting data access even at the field level. For example, the click-to-view feature provides access to data while also maintaining a log of what sensitive data was accessed when and by whom. The Appsian Security Platform takes a layered approach to security within your ERP ecosystem to enable field-level controls that prevent, restrict, and monitor access and modification of any field data.
Take a first-hand look at how Appsian can enable field-level controls in your ERP applications without disrupting business operations. Schedule a demo with our ERP experts.
Next in the Series: Ineffective Transaction Level Controls
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Material Weakness Series Part 1: Ineffective Access Controls
This is the first article of a multi-part series featuring material weaknesses. Each piece will focus on one critical internal control weakness and provide solutions on how to resolve the weakness with granular security controls.
The purpose of an independent audit of a company’s financial reports, called a Financial Statement Audit, is to form an opinion by the independent auditor if the current and potential investors can rely upon the accuracy and completeness of the company’s financial statement. During this audit, the auditors will evaluate the design and operating effectiveness of the internal controls intended to manage the risks relevant to maintaining the accuracy and completeness of the financial reports. The auditor may identify deficiencies in the company’s internal control over financial reporting, which will be ranked from lowest to highest impact as Control Deficiency, Significant Deficiency, or Material Level Weakness.
What is a Material Weakness?
According to the PCAOB, a material weakness is “a deficiency, or a combination of deficiencies, in internal control over financial reporting, such that there is a reasonable possibility that a material misstatement of the company’s annual or interim financial statements will not be prevented or detected on a timely basis.” Companies with material weaknesses are required to report them in their public SEC filings in the period in which they were identified. There are multiple types of internal control weaknesses that could lead to a material weakness.
Access Control Weakness
Segregation of duty (SoD) security violations are among the most common examples of an access control issue in ERP applications that lead to an auditor reporting a material-level control weakness. The principle of SoD is based on appropriately segregating critical duties to more than one person. For example, a single person should not have the ability to create and approve vendors, nor should that same person have the ability to create and approve payments. These four access rights could easily lead to fraudulent activity.
Resolving SoD Security Violations with Appsian
The avoidance of SoD security violations within your ERP application starts with an effective user-provisioning process that enables organizations to proactively analyze the role assignments to verify that no SoD violation exists before authorizing the access assignment. Unfortunately, most organizations use manual user provision processes that are tedious and error-prone.
Appsian automates your user-provisioning, de-provisioning, and access recertification process and enables real-time detection and prevention of SoD violations. The Appsian Security Platform also continuously monitors user behavior and authorization usage. This allows organizations to de-provision unused authorizations and flag sudden deviations in user activity, thereby reducing the overall risk and enhancing threat detection.
-
Define Scope of Process
Choose what and whom to review. Activities, Authorizations, Roles, Employees and System
-
Commence Review
A list of authorizations is sent for approval then facilitated to the next level of approvers
-
Complete Review
Upon reaching a well-grounded decision, the next level of approvers are able to confirm with just one click
-
Seal the Process
Upon completing the process, the results are sent to the security managers to implement changes
Some of the other leading practices offered by Appsian to prevent SoD violations include:
Policy-Based Access Control
With policy-based access, organizations can go beyond roles to implement controls based on contextual attributes. A policy-based access control security model improves your policy enforcement capability at the SoD level.
Identity & Access Management (IAM)
Authorization, being an integral part of IAM, allows you to increase the effectiveness of your user-access management lifecycle process. By implementing dynamic MFA at the login, page, and data field level, you can ensure sensitive data and transaction changes are logged and protected.
Identity Governance & Administration (IGA)
With real-time user monitoring, you can remove unnecessary authorizations while gaining governance and oversight of all user access to increase your ability to detect and prevent SoD violations.
The Appsian Security Platform gives you complete visibility and control of your ERP applications from the inside to resolve critical material control weaknesses. See the Appsian Security Platform in action by scheduling a demo.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Video Interview] David Vincent Talks to Security Guy TV About Improvements in ERP Security, Risk, and Compliance
Appsian Security’s Vice President of Product Strategy and Customer Experience, David Vincent, recently appeared on Security Guy TV to talk about ERP Security, Risk and Compliance and what organizations can do to further protect their data & business transactions.
Appsian.com with David Vincent at #GSX #GSC2021, Orlando on SecurityGuyTV.com from Security Guy TV.
Interview topics include:
- A brief overview of Appsian Security
- The challenges that corporate compliance officers face. At the top of their list is keeping up with an ever-changing regulatory environment.
- How system authentication has improved
- General improvements in ERP security
- How ERP security, risk & compliance “Policy Management” has improved
- The control frameworks that organizations are using to implement more effective ERP security, risk, and compliance programs
To learn more about how Appsian Security can help you manage and reach your ERP security, risk, and compliance objectives around your various application environments, contact us for a demo today.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
SAP Access Management: Automating and Centralizing the Identity Lifecycle
If you do an internet search for the most common cause of data breaches, you’re going to get a variety of answers: ransomware, phishing attacks, stolen credentials, insider activity, etc. While these types of cyberattacks lead to data breaches, there is one simple truth ERP customers can never overlook: data breaches are caused by unauthorized access. Of course, not all unauthorized access is malicious. It can also be accidental due to poor access management (also called identity lifecycle management).
Clearly, the best practice is using the principle of least privilege to grant access to the applications, transactions, and data that a person needs to carry out their jobs. While data security and privacy are the primary elements of a successful access management process, the overall identity lifecycle management process should be automated, centralized, and provide IT teams and business units with audit-ready information. This information is critical for providing reasonable assurances that their SAP access management process is compliant and operating effectively.
Poor Access Management Exposes SAP Data to Risk
The process of SAP access management shouldn’t exist in a vacuum or a silo. Unfortunately, many organizations struggle with manual and decentralized identity lifecycle management. This leads to a variety of situations where unauthorized access leaves valuable ERP data exposed to risk:
- Unused new accounts with default passwords
- Employees collect new authorizations as they move around the business without removing unnecessary ones
- New employee authorizations causing SoD issues and sensitive access issues
- Employees leaving the company while their user IDs remain valid
- And many more
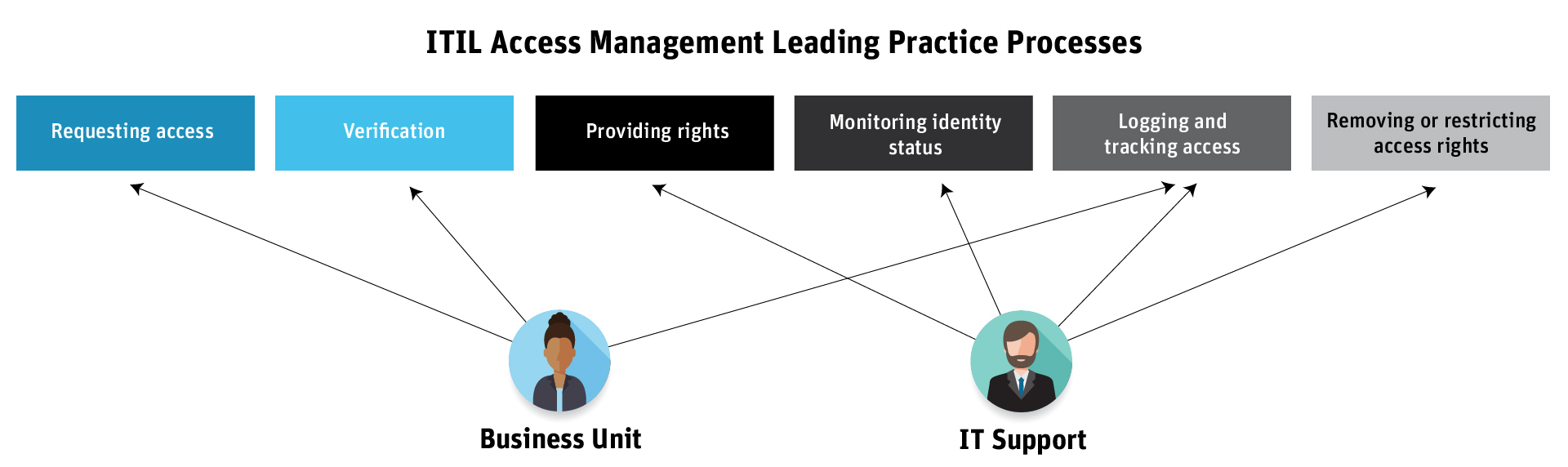
The identity lifecycle requires a process for controlling user access to critical information within an organization. The IT Infrastructure Library (ITIL) has a framework of best practices for access management: Requesting access, verification, providing rights, monitoring identity status, logging and tracking access, and removing or restricting access rights. But one department isn’t more responsible for the access management process than another, as outlined in this diagram:
While business leaders are the first line of defense and are responsible for owning and managing their risks, those business unit leaders and the IT departments are responsible for assigning and monitoring user privileges in ERP systems. Unfortunately, existing access management processes are manual, siloed, and error-prone. For instance, HR might request access by emailing IT or using a self-service portal to create a request. IT might use a provisioning solution that’s included out-of-the-box with their ERP system. But this approach is still mostly manual and exists in siloes, requiring one unit to rely on each other for updates.
This less-than-optimal approach leaves organizations exposed to security and compliance issues. Increasingly, organizations are under regulatory pressure to prove they are protecting access to corporate resources. As a result, organizations can no longer rely on manual and error-prone processes to assign and track user privileges.
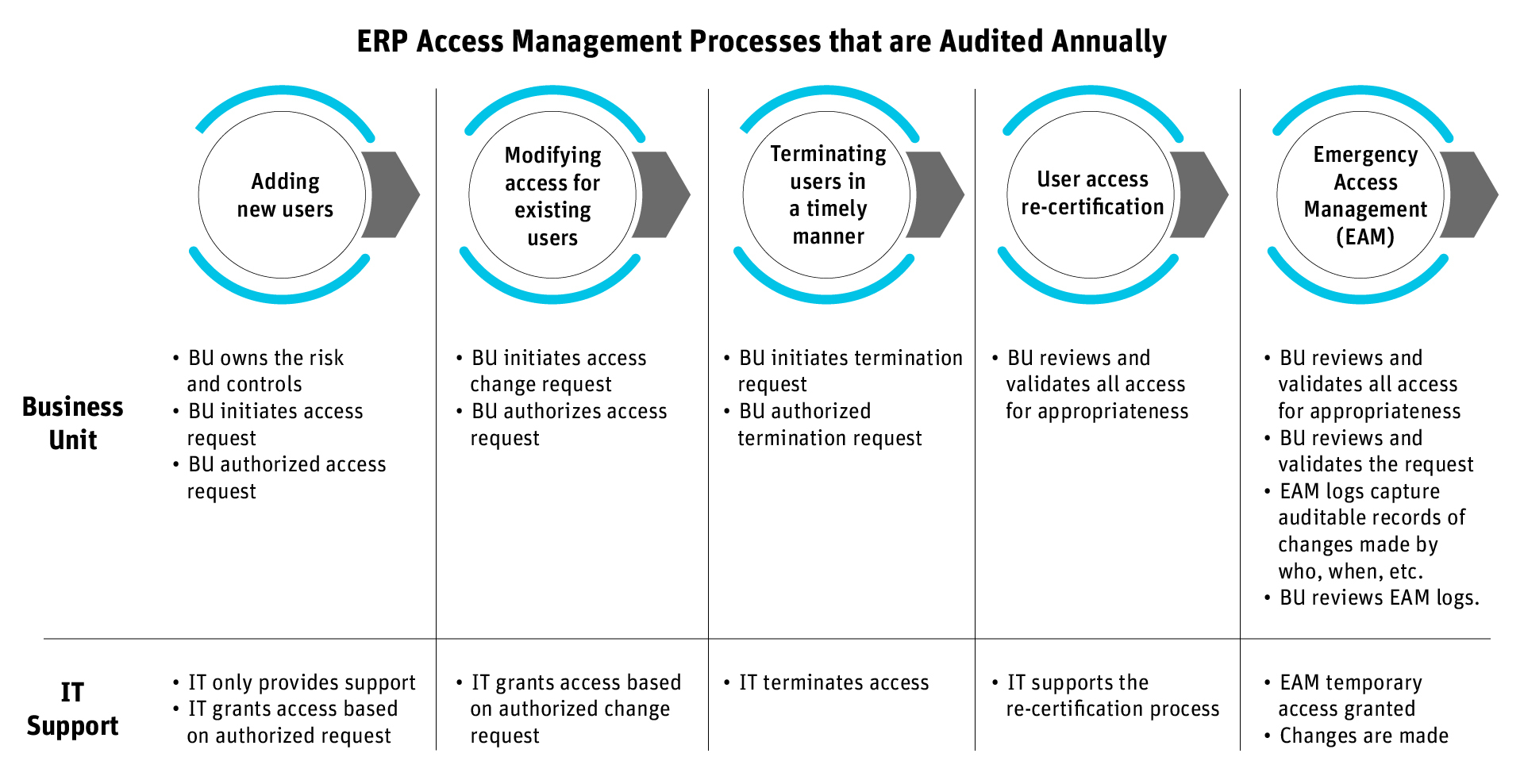
Audit-Ready Access Management
A poorly managed identity lifecycle process not only leads to security gaps but also visibility and compliance gaps.
As you can see from this illustration, all departments involved with access management will be audited to prove that their internal processes’ operating effectiveness sufficiently manages access risks, data security risks, and data privacy risks.
What’s missing for many organizations is an access management solution that centralizes and automates these tasks and enables granular access control and auditing of this process.
Automating and Centralizing Access Management with the Appsian Security Platform
Taking control of SAP access management from the start is key to enforcing data security, maintaining internal and external compliance, and adhering to various regulations. With ProfileTailor GRC from Appsian Security, you can easily organize, understand, and control the identity lifecycle process across your ERP landscape. Enabled by artificial intelligence, machine learning, and predictive analytics, it continuously identifies potential risks and provides optimized suggestions to streamline access management, including:
- Recommending the best alternatives when activities need to be removed from a user.
- Recommending the optimal segregation of roles to sub-roles according to business needs and actual usage. It automatically locks and removes the old authorization role from users who had it before the split.
- Solving SoD violations by replacing a user’s current roles without losing access to the activities actually needed.
- Choosing the optimal authorization role to grant users that enables them to perform additional activities without violating SoD policies.
Contact the SAP experts at Appsian Security for a demonstration on how you can prevent unauthorized user access at the transaction and master data level.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How ProfileTailor GRC Helped Global Shipping Leader, ZIM, Streamline Segregation Of Duties And Authorizations in SAP
ZIM Integrated Shipping Services Ltd., commonly known as ZIM, is a publicly held Israeli global container liner shipping company. The company operates over 100 management systems spread across the company’s global offices. Each system has multiple users running numerous applications, all consisting of different authorization systems. This scattered approach eventually led to siloed teams operating with their own rulesets and segregation of duties (SoD) policies, which stood in the way of effective internal audits within stipulated timelines.
The decentralized teams at ZIM needed a comprehensive GRC solution to streamline SoD, standardize context-aware controls, and customize authorization management solutions for their different locations without impeding productivity. Specifically, they needed a system that would:
- Control authorizations in a multi-regional, multi-system environment
- Manage authorization related processes effectively on all systems worldwide
- Comply with SoD in a complex environment
- Monitor activity in production systems
So the company turned to Appsian Security’s ProfileTailor GRC solution to improve their global, multi-system authorization layout and improve GRC compliance.
ZIM’s Transformation From Siloed To Centralized
ZIM’s transformation from siloed to centralized did not happen overnight. It was a large-scale, global roll-out with multiple milestones that Appsian played an integral part in.
Centralizing Control & Visibility Over Global Authorizations: ZIM now has centralized control over global authorizations in their complex multi-system environment with Appsian’s ProfileTailor GRC Solution. Additionally, they have generated Employee Cards consisting of authorizations on all applications from a single point of view. This is providing visibility to relevant managers in every location.
Identifying SoD Violations: ZIM’s BMC Remedy IT Management System seamlessly integrated with Appsian’s solution in the next phase. As a result, ZIM can now stop potential SoD violations in their tracks at the early stage of requesting authorizations, helping their teams streamline Segregation of Duties and stay compliant in the long run.
Automating & Customizing Authorization Review Process: With their authorization request policies cleaned up, unified, and customized for each location, ZIM is now operating with an automated authorization review process without disrupting the workflow. They are also able to save overhead expenses and have become audit-ready.
The Last Mile – Standardizing Contextual Access Controls: Presently, ZIM is equipped to control the access of the IT teams into production systems. With Appsian’s ProfileTailor GRC, they can now continuously monitor users in the production environment and allocate temporary roles for specific tasks.
Their teams can standardize every process in terms of access, authorizations, and policies while allowing exceptions (e.g., specific data privacy regulations) based on locations.
Streamline, Standardize, Customize: Appsian’s Framework Could Benefit You Too
Through a series of successful implementations with the help of Appsian Security, ZIM is now –
- Streamlining Segregation of Duties
- Standardizing context-aware controls
- Customizing for each region without workflow disruption
If your organization is working with siloed teams engaged in manual audits and approval processes, Appsian’s ProfileTailor GRC Suite is your one-stop solution to gain better control over access risks, SoD, compliance, and audit. It can be used as a stand-alone solution for streamlining, managing, and enforcing SoD or as part of a suite of compliance products.
ProfileTailor GRC is compatible with all leading ERP applications, including SAP, Oracle E-Business Suite, Oracle PeopleSoft, Microsoft Dynamics, and more. Best yet, it can be implemented rapidly and will not require any changes to monitored systems.
Contact us for a customized demonstration today and find out how Appsian Security can help you.
Related Reading: Full ZIM Case Study
Image source: Wikimedia Commons
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How Appsian Approaches Cross-Application SoD for SAP, Oracle & More
The concept of segregation of duties for SAP and other ERP applications is simple to understand: ensure that a user’s access privileges do not conflict or violate business policies and divide business processes between multiple users to limit the risk of fraud and error. However, the streamlining, managing, and enforcing of segregation of duties is far more complex. These days, organizations are turning to technology to help them automate tedious manual processes and reinforce internal controls—technology like Appsian.
Enforce Cross-Application SoD Rulesets from A Single Control Point
Appsian is a single control point that enforces cross-application SoD rules – allowing auditors and security managers to implement one SoD ruleset and enforce it on multiple applications simultaneously. They can also create rulesets for specific systems or change, activate, or deactivate SoD rules that can influence all systems together or only particular systems. Essentially, ProfileTailor GRC unifies all applications into one “language” so auditors and security managers do not have to try to understand each application’s jargon while giving them complete control over their SoD compliance, helping them comply with SOX regulations.
Maintain, Upload, and Download Rulesets in Multiple Schemas to Fit Different Scenarios
Ruleset maintenance is a focal point of any SoD implementation. ProfileTailor GRC includes various methods to create and maintain SoD rulesets easily and effectively to maximize the level of control over segregation of duties. For example, auditors can prepare a ruleset, upload it using a built-in mechanism, and then maintain the rules inside the application.
Alternatively, they can create rules in the application and then maintain, download, and upload them to Excel sheets. Further, auditors can lock specific rules for editing while allowing others to be opened. Business units can edit their own ruleset while being able only to view the organization’s global ruleset. Additionally, ProfileTailor GRC comes with a predefined ruleset that is ready for customization so organizations can be up and running almost immediately.
Resolve SoD Conflicts in Seconds
The best way to handle SoD violations is to solve them clearly and quickly. ProfileTailor GRC analyzes user behavior and usage data paired together with vast amounts of hands-on experience in the field of risk assessment to resolve SoD conflicts in just a few seconds. ProfileTailor GRC can audit violation events in real-time because it assesses SoD risks and violations based on users’ actual usage, not only on their given authorizations, and recommends the best solution for solving the violation and up to 5 additional possible solutions
Make ProfileTailor GRC a Critical Part of Your Compliance Strategies
ProfileTailor GRC can be used as a stand-alone solution for streamlining, managing, and enforcing SoD or as part of a suite of compliance products. This means that enforcing an SoD ruleset will influence other workflow processes. For example, provisioning/de-provisioning user accounts, requesting new authorizations and preventing SoD conflicts, opening new user accounts automatically without SoD violations, and business rules for granting or revoking authorization roles.
ProfileTailor GRC is compatible with all leading ERP applications, including SAP, Oracle E-Business Suite, Oracle PeopleSoft, Microsoft Dynamics, and more. It can be installed as an on-premise solution for continuous protection or in the cloud as a continuous inspection solution.
For more information on how ProfileTailor GRC approaches segregation of duties for SAP and Oracle ERPs or to receive a customized demonstration, please go HERE.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives